Detecting Android App Collusion with FUSE
FUSE (Field Unit Security Enforcer) helps security analysts see how a collection of apps operates together in the context of a full Android device. FUSE provides an overview of a collection of apps, showing the potential data flows within that collection.Try Using FUSE Now!
Check out the Quick Reference and then use the links below to use our interactive analysis:
The Android security model was built from the ground up to combat potential attacks (or misuse) one app at a time. This model culminates in a user interface that asks for the user’s approval each time an app is installed. While the interfaces enables users to avoid applications that may violate their security policy (by using combinations of permissions) applications can freely communicate with each other to share their permissions, achieving capabilities through collusion that astute users would not have approved.
A holistic view of the app ecosystem is necessary to identify these potential collusions, but no existing tools provide such an interface. Galois has been working with DARPA to develop a system that enables security analysts to quickly examine collections of Android apps, focusing their analysis on sets of apps that may be sharing capabilities (either intentionally or inadvertently) that result in undesirable data flows and possibly exfiltration.
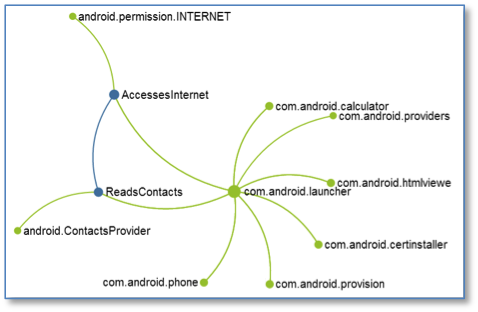
FUSE visualizes data flow, showing that ReadsContacts colludes with AccessesInternet to subvert single-app analysis.The resulting tool, called FUSE, conducts a binary static analysis of individual Android apps to identify inputs and outputs. FUSE then produces an Extended Manifest that concretely defines the possible set of sources and sinks for a given app. An additional multi-app analysis connects compatible sources and sinks and presents users with an interactive interface where they can delve into the possible data flows for a given device.
App Collusion: Subtle Exfiltration
FUSE combines information from the static analysis of multiple apps to give security analysts the ability to quickly see where collusion or other undesirable interaction may occur—interactions that no single-app analysis can reveal. Analysts can combine the information from the resulting visual data flow graphs with their expert domain knowledge to focus their attention on the applications that pose the greatest risk.
The FUSE tool is also interactive: Analysts can filter different types of data flow, select subsets of apps, and dive into the details, revealing the bytecode locations responsible for data transfer.
No Source Needed
The FUSE analysis runs on compiled Android APKs, meaning you can run FUSE on any Android application, and FUSE integrates seamlessly into your existing development workflows.
FUSE also works with third-party apps because it operates on APKs directly, with full support for all the FUSE features:
- Examine all data flow paths possible in a collection of Android apps.
- Identify the specific methods responsible for data flows.
- Filter by customizing the visible data flow types and hiding trusted nodes to focus on potentially dangerous capabilities.
Read More
Check out the Quick Reference and then use the links below to use our interactive analysis: