3DCoP: DDoS Defense for a Community of Peers
Modern Distributed Denial of Service (DDoS) attacks are too big for medium-sized organizations to handle, as the amount of traffic generated is sufficient to saturate their Internet connections. Once an organization’s network connection is saturated, local mitigation is no longer possible. This class of attack thus threatens critical infrastructure, such as financial institutions, news organizations, and government agencies. Current DDoS defense systems fail to address this problem because they operate in isolation, which introduces delays in the detection, reporting, and response to a DDoS attack. The delay in responding to an attack is critical: it provides positive feedback to the attacker, who will continue to send more and more traffic at the target network. This, in turn, increases the difficulty in mitigating the attack.
To address these delays, 3DCoP uses a unique collaborative model wherein multiple organizations work together to detect DDoS attacks, compute mitigations, and convince service providers to take action. Our solution advances the state of DDoS defense by providing new tools that allow multiple defenders to coordinate their response, resulting in earlier detection and faster DDoS mitigation. Underlying our implementation is a unique traffic flow monitoring capability, which observes traffic flows in and out of the enclave and finds patterns of interest.
3DCoP then transmits these discovered patterns via a peer-to-peer collaboration mechanism that can compute a more complete view of the network. As a result, rather than having a single, small entity requesting a rule change of a major ISP, we create a large virtual organization that acts with consensus.
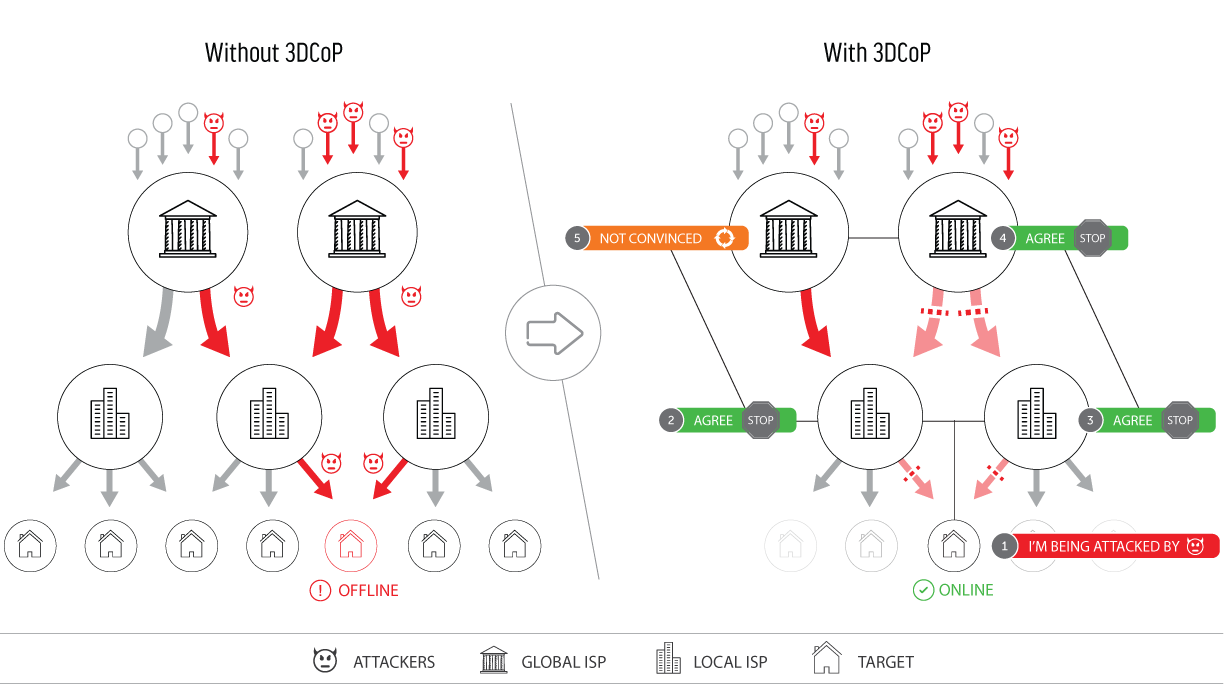
As a result of our work, we aim to reduce mitigation response time by 50%, resulting in peak traffic reduction of 75% – 90%. Additionally, we plan to reduce the time between the start of the attack and the detection of the attack by 25%. As a result of these reductions, organizations will be able to detect and block DDoS attacks before reaching complete network saturation. Safety- and business-critical institutions will also be provided advance notification and information required to take action even during peak periods of the attack; for example, they can switch to operating modes that prioritize their most critical communications.
This project is the result of funding provided by the Science and Technology Directorate of the United States Department of Homeland Security under contract number D15PC00185. The views and conclusions contained herein are those of the authors and should not be interpreted as necessarily representing the official policies or endorsements, either expressed or implied, of the Department of Homeland Security, or the U.S. Government.